Today, cyber threats are an essential part of corporate risk regardless of company size or industry. Our primary goal is to fully protect our customers from cyber threats of all kinds. Our cybersecurity and data protection offering fully covers strategy, design and, of course, implementation.
FULLY COMPREHENSIVE CYBERSECURITY AND DATA PROTECTION
Your advantages
- PROTECTION OF YOUR DATA AND KNOW-HOW AS THE PRIMARY GOAL
- MODERN SECURITY STACK FOR BEST POSSIBLE PROTECTION
- EXPERIENCED ENTERPRISE CYBER DEFENSE TEAM AVAILABLE AT ALL TIMES
- NUMEROUS CERTIFICATIONS GUARANTEE COMPLIANCE WITH THE LATEST STANDARDS
- CONSULTING AND SUPPORT FOR OWN SAFETY CERTIFICATIONS
- LOW RISK OF ATTACKS THANKS TO PRIVATE CLOUD
FULLY COMPREHENSIVE CYBER SECURITY
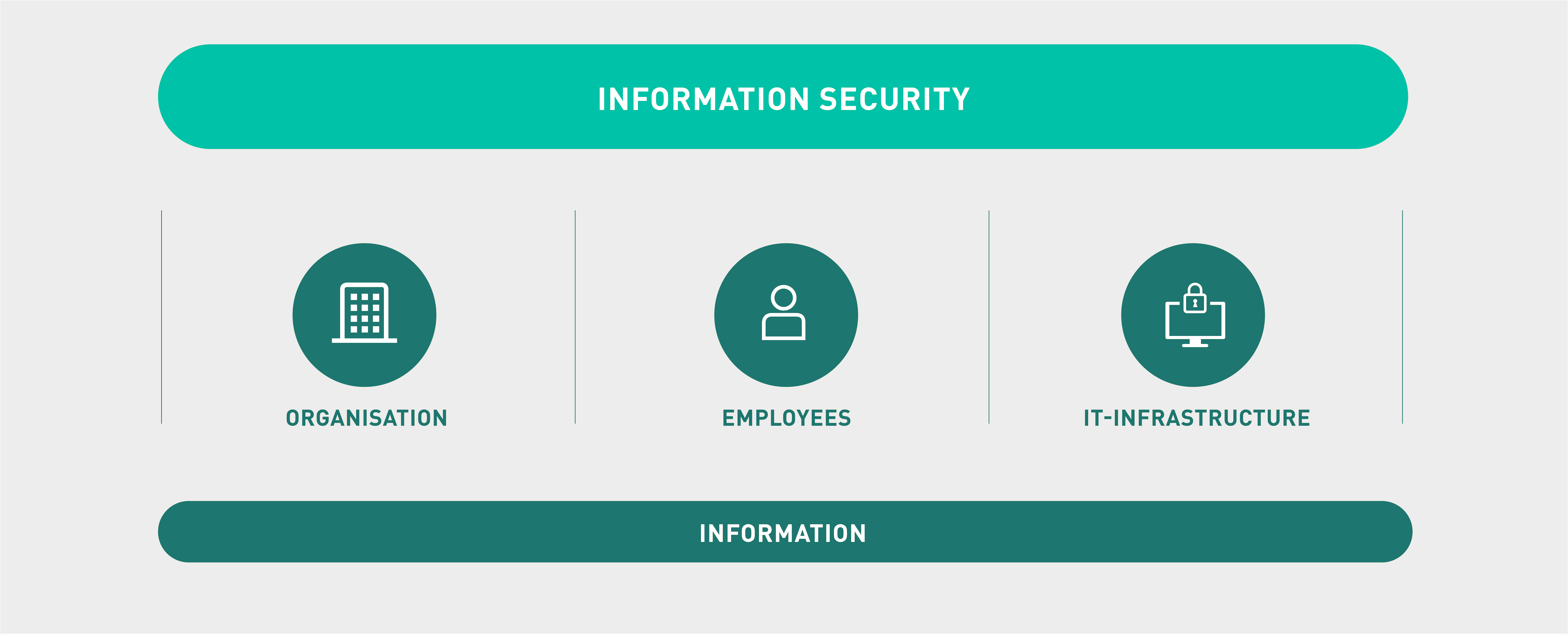
Our fully comprehensive security stack provides maximum information security for enterprises. We use numerous physical, infrastructural and operational procedures and also assist you with information security certifications, insurance issues or awareness training. Our experienced Enterprise Cyber Defense team works around the clock to proactively counter new threats and intervene immediately in emergencies.
FULLY COMPREHENSIVE CYBER SECURITY
Our fully comprehensive security stack provides maximum information security for enterprises. We use numerous physical, infrastructural and operational procedures and also assist you with information security certifications, insurance issues or awareness training. Our experienced Enterprise Cyber Defense team works around the clock to proactively counter new threats and intervene immediately in emergencies.

CERTIFIED SAFETY STACK
SECURITY STACK STANDARDS
MTF Cloud's fully comprehensive security framework is based on security standards including:
- ISO 27001, 27017 and 27018
- ISO 22301
- NIST Cybersecurity Framework
- OSSTMM
- OWASP
- ITIL
- COBIT
- PCI DSS
- IT Basic protection
TECHNICAL FUNCTIONS OF THE SECURITY STACK
- Active or Passive DDOS Protection (DDOS)
- Next-Gen Distributed and Multi-Tiered Firewalls
- Intrusion Detection and Prevention System (IDS / IPS)
- Advanced threat detection based on artificial intelligence
- Anti-ransomware and exploit prevention
- Antimalware with deep learning technology
- Endpoint Detection and Response (EDR)
- Security Information and Event Management (SIEM)
- Email signing, encryption and filtering
- Next-Gen Web Reputation and Web Filtering
- Enterprise Cyber Defense Center with Emergency Response Team