Cybersecurity during Carnival: Digital freedom to act foolishly?
Whether it's the Morgenstreich in Basel or the Urknall in Lucerne – when the fools are let loose, costumes and deception are the order of the day. But what is fun during the ‘fifth season’ is a serious threat in everyday digital life: cybercriminals use similar methods – only with far more unpleasant consequences.
When the masks are put on and the Grendel costumes are donned, and the sound of Guggen music booms through the streets, chaos reigns – but with a system. People slip into roles, hide their true selves and use the general exuberance to break down barriers. What creates the atmosphere between Barfüsserplatz and Kapellplatz is one of the most dangerous strategies used by cybercriminals in the digital world: targeted manipulation.
It's all in the mask: social engineering as digital disguise
At Fasnacht, no one questions who is really under the costume. Hackers use precisely this principle in social engineering: they manipulate people rather than software. They slip into roles that inspire trust – from the supposed CEO who requests an urgent transfer by email to the ‘new colleague’ who asks for access data in a chat because he has allegedly forgotten his batch.
The difference to carnival: in cyber attacks, the deception is often only recognised when the account is empty or the network is encrypted.
Social engineering: When hackers slip on their costumes
Instead of technical vulnerabilities, attackers use psychological tricks – like a clever masquerader at a parade or the Lucerne procession. These are the most common methods:
- Phishing: Fake emails that lure you to fraudulent websites.
- Vishing (voice phishing): Telephone deception by alleged support staff.
- Pretexting: Invented scenarios to elicit sensitive information from you.
- Baiting: ‘Bait’ such as infected USB sticks on company premises.
- Tailgating: Physically ‘tagging along’ through the security door in the slipstream of employees.
A frightening fact: over 90% of all successful attacks today begin this way. Even the strongest security door is useless if you politely hand the key to the wrong person.
In an upcoming article, we will explain these methods in more detail and show you how to make your team crisis-proof.
The fool knows no rules – neither do cybercriminals
During carnival season, the normal rules are suspended. What would otherwise be considered rude or inappropriate is suddenly permitted. Cyber attackers behave in a similar way: they exploit every vulnerability, ignore every ethical boundary and strike when no one is expecting it.
Popular times for attacks:
- Holiday periods: IT teams are reduced in size – perfect for an undisturbed attack.
- After work or at the weekend: when no one is at their desk, hackers dance on the server.
- During major events or crises: when attention (or the entire workforce) is elsewhere, the digital attack follows.
While carnival pranks are over by Ash Wednesday at the latest, the consequences of cyber attacks can reverberate for months. That's when the fun definitely stops.
Confetti & chaos: when you lose track of things
During the parade, there is controlled chaos. Thousands of confetti pieces fly through the air, it is loud and confusing. This is exactly what modern cyber attacks do: they overwhelm defence systems with massive requests (DDoS), hide malware in harmless files or disguise themselves as legitimate data traffic. In the flood of information, it is easy to overlook the crucial warning signs.
The ‘party hit’ of cybercriminals: ransomware
When we talk about the risk of masquerades and chaos, we inevitably end up with the final boss: ransomware.
Imagine someone sneaking into your house during the move and quietly replacing all the door locks. The next morning, you stand in front of your own door, unable to access your valuables, and find only a note: ‘Pay us a hefty sum, or we'll throw away the key and publish all your private documents on the internet.’
This is exactly what happens digitally: the hacker locks all your data with a digital lock and demands a ransom for the decryption code. A glance at the current databases for security incidents shows that this is not a theoretical danger, but bitter reality:
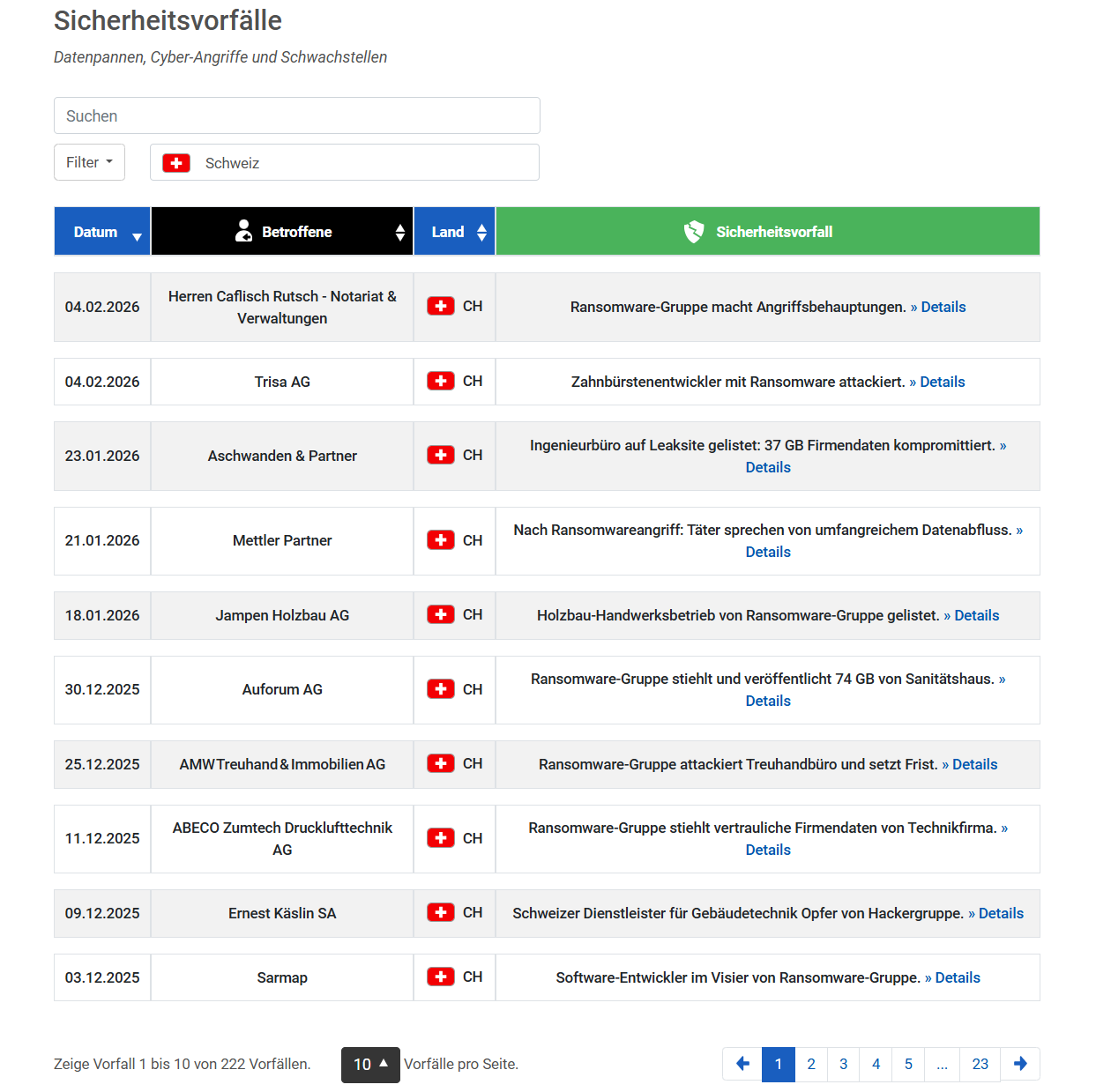
Almost every day, Swiss companies of all sizes and from all sectors fall victim to these attacks. Anyone who believes that SMEs are ‘too insignificant’ to be targeted is ignoring the facts – from local notaries to industrial companies, anyone who is unprotected is vulnerable today.
Media tip: When the ‘masquerade’ becomes serious
The impressive documentary by NZZ Format, ‘Pay Up or Perish,’ shows that cyber attacks are much more than just a technical nuisance.
The film follows Swiss entrepreneurs who have fallen victim to ransomware. It makes it clear that highly professional criminal organisations are behind the attacks. When your life's work is encrypted, the moral question becomes an existential question of survival.
Our recommendation: watch this documentary to see real-life examples of why cybersecurity is not just an IT buzzword, but a matter of pure survival.
After carnival: Security needs continuity
Carnival ends at the latest when the streets are swept clean on Ash Wednesday (or after the ‘Ändstraich’). Cybersecurity, on the other hand, knows no respite. While the costumes are being stowed away in the wardrobe, attackers are already developing new methods.
What Swiss SMEs should do now:
- Gain transparency: Put your digital defences through their paces.
- Raise awareness: Regularly sensitise employees so that they can recognise hackers' ‘Morgenstreich’ in good time.
- Multi-factor authentication (MFA): Your digital identity check that lifts the mask.
- Backup strategy: Use the 3-2-1-1-0 rule to keep your business crisis-proof.
- Monitoring: Detect attacks before they cause damage with a Security Operations Centre (SOC).
- Contingency plan: Does everyone involved know what to do when the music suddenly stops playing?
MTF: Your partner for cyber security
Dressing up is allowed – but only during carnival
Masks are as much a part of carnival as flour soup is to Basel and Fritschi is to Lucerne. In the digital world, however, they are warning signs. Those who recognise the parallels can better protect their companies. At MTF Solutions, we ensure that cybercriminals do not get the freedom they are entitled to during carnival. With Managed Security Services, we keep your network secure – so you can celebrate without worry.
Would you like to know how well your company is protected against digital masquerades? Contact us for a no-obligation security assessment.